IB Computer Science Vocabulary by Dave Mulkey, 2001, Germany
CHARLES BABBAGE
(1834) He conceived the basic structure and four main
components present
in virtually all computer systems:
CPU
= Central Processing Unit, i.e. Pentium
MAIN
STORAGE = RAM/ROM memory
INPUT
device(s) = i.e. keyboard, mouse
OUTPUT
device(s) = i.e. monitor, printer
Modern computers have
added BACKING STORE (disk drives) in most systems.
Most
business systems incorporate ARCHIVE STORAGE (tapes) as well.
In
the future, virtually all computers will COMMUNICATE (modem,
network)
with other computers.
BLOCK FUNCTIONAL DIAGRAM
= shows components and modules in a system, with lines showing connections between them
~ The diagram below shows the connections between
components in a Stand-Alone Computer System (LOCAL components)
+----------------------------------------------------------------------+
| INPUT CPU (Central Processing Unit) OUTPUT |
| +----------+ +----------------------------+ +--------+ |
| | Keyboard | |Arithmetic/Logic Unit (ALU) | | Monitor| |
| | Mouse |----->|............................|------->| Printer| |
| | Scanner | | Control Unit | | Speaker| |
| +----------+ +----------------------------+ +--------+ |
| | | |
| +-------------------------+ +------------+ |
| MAIN | RAM = programs and data | DMA | Hard-Disk | BACKING |
| STORE |.........................|<-------->|Floppy-Disk | STORE |
(internal)| ROM = operating system | Direct |Optical-Disk|(external)|
| +-------------------------+ Memory +------------+ |
| | Access | |
+------------------ Port -------------------------- Port --------------+
| |
+----------------+ +-----------+ ARCHIVAL
COMMUNICATIONS | Network Adapter| | Tape | STORAGE
(remote) | Modem | |"streamer" | (remote)
+----------------+ +-----------+
USER-INTERFACE
= how the user communicates with the computer system. Older
computers used a text-based, command-line system, e.g.
MS-DOS or UNIX, where the user must type commands.
Modern
computers use a Graphical User Inter (GUI).
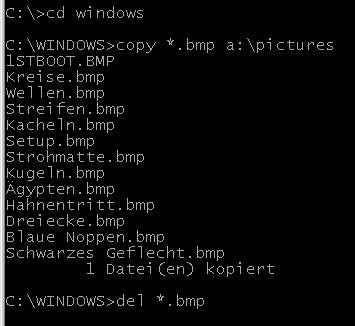 COMMAND-LINE
INTERFACE
COMMAND-LINE
INTERFACE
= a text-based interface for giving commands to the operating
system,
as in MSDOS or Linux.
Users must type commands, often using strange words and symbols.
This was popular until the 1980's, when GUI's became popular.
The commands in the picture:
- change to the Windows
directory
- copy all .BMP files to the floppy
- delete
all the .BMP files from
the
c:\windows directory.
GUI
~ MS-Windows, MacIntosh, X-Windows (UNIX).
= Graphical User Interface
Icons (pictures) represent files and directories. A mouse is used to give commands.
Another name for this is WIMP – Windows, Icons, Menus, Pointer (mouse).
The GUI improves standardization across applications. Each OS contains many standard subroutines that applications can use, so applications from different software companies still present similar interfaces. This makes things much easier for the users. For example, most Windows applications use the same standard File-Open and File-Save dialogs.
MULTI-MEDIA
~ Encyclopedia on a CD-ROM
= a system with a large variety of I/O (input/output) modes
and devices,
that work together to produce a complex "natural"
interface.
Multimedia presentations usually include most of
the following:
text , sound , graphics ,
animation , video
CPU
= Central Processing Unit.
In a PC, it's the microprocessor, e.g. Pentium chip.
In
a main-frame, the CPU is the main unit (box), a large
version of a PC box.
It often contains many microprocessors,
but does not contain disk drives.
The CPU is divided into two sections: ALU and CU
ALU (Arithmetic Logic Unit) | CU (Control Unit)
Registers | Address Bus Controller
Arithmetic Circuits | Data Bus Controller
Logic Circuits | Interrupt Controller
The ALU does arithmetic calculations and evaluates Boolean
operations (decisions).
The CU controls communication
between the CPU and RAM and other chips.
PRIMARY MEMORY
Main memory - where running programs and active data
are stored.
This includes RAM and ROM. The RAM
is volatile (changeable) and is erased
whenever the
power is turned off. The ROM is non-volatile (permanent).
Memory is divided up into bytes (8 bits) and words
(16 or 32 bits).
Memory works like an array – each
memory location has an address and a value.
In
some programming languages, the memory can be accessed directly,
by a command like: MEM[12345]
= 65
which places the value 65 into memory location
#12345.
SECONDARY MEMORY
Permanent storage, including hard-disks, floppy diskettes, tape drives, Cds.
In pocket-size computers, flash memory is used as
secondary memory, as disk-drives
would be too large.
ROM
Read Only Memory.
Permanent (non-erasable) memory containing lots of low-level operating system routines.
Contains the BIOS (Basic Input/Output System), including the BOOT routines which are the first programs to run when the computer is powered on.
Generally these BIOS routines are never changed, but some newer PCs use FLASH EPROMs which can be upgraded.
FLASH EPROM
Erasable Programmable Read Only Memory
ROM is permanent and cannot be changed. Flash EPROMs can be reprogrammed. The entire chip (i.e. 64 Kb) is erased at once (by an electric current or ultra-violet light) then rewritten all at once. This is a dangerous process. If the computer crashes during this process, it can never be restarted. A BIOS upgrade is usually only necessary if very new hardware is added to the system (e.g. Very large hard-disks, strange I/O devices, etc.)
BIOS
Basic Input/Output System
Contains lots of low-level subroutines written in machine
language.
These manage low-level control of hardware - i.e.
reading/writing a disk sector,
updating the system clock,
accepting keyboard input, etc.
RAM
Random Access Memory
The main part of the computer's memory. This can be changed easily and is used for storing programs and data (temporarily) inside the computer, when programs are running.
VIRTUAL MEMORY
When main memory gets full, the OS can swap some of the
contents
onto the hard-disk (into a temporary file) to free up
some memory space,
to load other programs or data. When
needed again, the data in the temporary
file is swapped back
into main memory. This is much slower than using
main memory,
but creates a virtually unlimited amount of memory.
Old
operating systems (like DOS) did not support this, but all
modern
multi-tasking systems support it (Windows,
Linux, MacOS)
INPUT DEVICE
Hardware for getting data into the computer, most
commonly:
--> keyboard, mouse, joy-stick,
microphone, light-pen, scanner
LIGHT PEN
an input device shaped like a stylus (pen), containing an
optical sensor,
which can be used to draw directly on the
computer screen.
BAR-CODE-READER
Uses a laser beam to read the stripe-codes found
on
manufactured packages - you see these
in use in the grocery
store at the check-out counter.
GRAPHICS TABLET
a pressure-sensitive (or electro-magnetic sensitive) drawing
surface -
you draw on this with a special stylus (pen) to
input a picture.
As you draw, the picture appears on the
screen.
This is more comfortable to use than a mouse.
SCANNER
works like a photocopier, to input a photograph or a printed
page.
Together with OCR software, this can input a printed
paper document
and change the picture into a word-processing
document.
OPTICAL CHARACTER RECOGNITION
OCR - software that functions together with a scanner,
to change a bit-mapped picture from the scanner
into a
text-file of ASCII codes.
OCR is a very difficult process for the computer.
It must
recognize letters, which may appear in any
font or
size. If the page is not perfectly straight,
the letters may
be slightly tilted.
The printed document may also be faded,
or it may be a photocopy with lots of dirty grey areas.
MAGNETIC INK CHARACTER RECOGNITION
MICR - the strangely shaped letters on the bottom of
personal checks.
These are read by a magnetic scanner - not by
an optical scanner.
OUTPUT DEVICE
Hardware for getting data out of the computer, most commonly
:
--> monitor, printer, speaker, plotter, flashing lights
PLOTTER
it draws pictures by moving a pen around on a sheet of paper.
Uses two
motors to control vertical and horizontal motion
independently. This
is better than a printer, because it can
draw straight lines and curves
without jaggies, since it uses
a real pen instead of dots.
MONITOR
the computer's screen, also known as a CRT, VDU, or LCD
VDU
Visual Display Unit
CRT
Cathode Ray Tube
LCD
Liquid Crystal Display, found in pocket calculators and notebooks
STORAGE DEVICE
hardware where data can be saved and retrieved later,
commonly:
Hard-disk, floppy diskette, tape-drive (streamer)
FLASH-EEPROM
Electrically erasable programmable ROM, which can be erased
rewritten
INSIDE the computer. A FLASH of electrical current
does the erasing,
erasing the ENTIRE contents, which is then
TOTALLY rewritten
WORM
Write Once, Read Many - a type of CD disk in which large
amounts of data
are written once, and then accessed many
times. This is not sensible for
data-bases which are
frequently changed.
ARCHIVE
storing information off-line, for example on a tape
which is not
in the computer. An archive file might contain
old records which are
no longer used, but need to be kept for
historical or legal reasons,
or they may contain backup copies
of important data. Archives should
be kept far away from the
computer, so that fire, sabotage, or theft
cannot effect BOTH
the original copy (in the computer) and the archive.
PERIPHERALS
Keyboard, printers, plotter, scanner, etc. Other "extra"
pieces which
are not an integral part of the main unit.
MODEM
MOdulator-DEModulator - an interface between a PC and a
telephone. The
modem translates the computer's DIGITAL signals
into ANALOG sound waves
which can be transmitted over
telephone lines. At the other end,
another modem translates
the signals back to digital for another
computer to use.
DUMB TERMINAL
a keyboard and monitor used to communicate with a central
computer.
The user only has the input and output devices at
his/her desk - the
computer itself is somewhere else. Earlier
terminals consisted of a
TELETYPE - an electric typewriter,
printing on paper.
MICROPROCESSOR
a chip that can perform many complex functions, usually
including
input, output, and arithmetic. A microcomputer
contains many
microprocessors - the CPU, a keyboard controller
chip, several to
control the disk drive, a graphics chip, etc.
BUS
the circuits which carry signals from one chip to another. The
CPU puts
an address on the ADDRESS BUS, and receives data back
from the memory on
the DATA BUS. A "true" 16 bit
microcomputer has a data bus with 16
circuit lines. 386SX
computers have 32-bit registers, but only a 16 bit
data bus.
This is slower, but cheaper to build. A 486 is a "true"
32
bit processor, using a 32 bit data bus. Modern Pentium
based computers use a 64-bit databus, thus transferring 2 full
32-bit words at a time. PCI boards provide a bus linking the
memory directly to the I/O cards, bypassing the CPU and allowing
I/O to continue at the same time the CPU does something else.
DIRECT MEMORY ACCESS
DMA - this allows a peripheral device (e.g. disk drive
or graphics card)
to read and write data to the RAM, without
sending through the CPU.
This allows the CPU to continue
running a program, simultaneous with
I/O operations.
BANDWIDTH
the total amount of data which can be transmitted per second.
A typical 56 KiloBit modem has transmits 7 KiloBytes per
second.
A mother board running at 100 MHz with a 64 bit data
bus can
transfer 8x100 = 800 MegaBytes per second.
Two ways to increase bandwidth are:
1 – increase the
signal frequency
2 – increase the bus width
Recently PCs have appeared with a
faster front-side-bus (FSB) running at 233 Mhz,
instead
of the old 66 Mhz and 100 Mhz machines.
Larger bandwidth is the biggest improvement required to support multimedia applications.
BUFFER
temporary memory for accepting data from another device. This
is
especially useful for connecting a fast device to a slower
one.
A printer uses a 4 MB buffer to quickly accept all the
data for a
print job, and then prints this data to paper
while allowing the
computer to continue with other tasks.
When you watch streaming video on the Internet, the browser will buffer several seconds of the video before it starts showing it. Then if the video stream gets interrupted or slows down, the computer can continue playing the video at the correct speed while waiting for the data.
DOUBLE-BUFFERING
using 2 buffers - one is being filled with new data at the
same time
that the other is being emptied. This is common with
faster devices such as hard-disks, allowing the system to
continue transmitting at the same time as the disk-drive is
writing the data. This isn't very useful if the device is slow,
as both buffers quickly become full anyway.
BIT
BInary digiT. This is the smallest unit of computer memory. It
can
contain a value of 0 or 1. Every bit is physically
represented by 1
transistor. In old computers, a bit was
represented by a magnetic
"core" - a tiny magnetic
ring magnetized in one polarity or the other.
BYTE
The smallest addressable unit of computer memory. It is not
possible to
store a single bit in memory - an entire byte most
be loaded into the
CPU, a single bit changed, and the entire
byte stored back into memory.
In most computers, 1 byte = 8
bits , storing a value between 0 and 255.
WORD
The size of a register, thus the standard amount of data for
arithmetic
operations. In a "16 bit" computer, 1
word = 2 bytes = 16 bits. A
word could be used to store a
value between $0000 - $FFFF, which is
0 - 65535 in decimal. In
a "32 bit" computer, registers are 32 bits
"wide",
and so 32 bits can be added to 32 bits in one step.
REGISTER
a memory location inside the CPU. Registers can be used to
do
arithmetic, logical operations, or temporarily hold
results. To add two
memory locations together, both values are
copied into registers, the
registers are added, and the answer
stored back into memory.
KILOBYTE
(KB) Actually 1024 bytes, not 1000. 1024 = 2^10 . In binary,
powers of 2 is are "round" numbers, rather than
powers of 10 (decimal)
A 56 K modem is NOT 56 KB per second,
but rather 56 Kb (kilo-bits),
which is 7 KB per second.
MEGABYTE
(MB) 2^20 = 1048576 bytes. The capacity of a 3.5" floppy
diskette
is 1.44 MB. An old fashioned hard-disk holds 40 MB.
GIGABYTE
(GB) 2^30 bytes - the approximate capacity of a modern hard-disk
TERABYTE
(TB) 2^40 bytes - a storage capacity for the next generation
of
computers, which will commonly use multimedia environments
ADDRESS
(memory location) a number which tells WHERE something is
stored in the
computer's memory. Every byte has its own
address. In the original
IBM PCs, the addresses were 20 bits
long, allowing addresses up to
1 Megabyte, but 64 KB was
allocated to the graphics-card, another 64 KB
was allocated to
the ROM BIOS, 128 KB was reserved for expansion. In
the end,
MS-DOS was restricted to 640 KB - "conventional memory".
This
was adequate in the 1980's, but not adequate for
graphical-user-
interfaces (GUIs). Modern PCs use 32 bit
addresses, allowing access to
2^32 bytes of memory (4
GigaBytes).
VON NEUMANN ARCHITECTURE
MEMORY
+---------+
+-----+ | Program |
| CPU |<---->|---------|
+-----+ | Data |
+---------+
John Von Neumann (1945) is responsible for the basic concept
of most
modern computers. There is a single CPU (Central
Processing Unit), which
does the following:
- Fetch the next instruction from the
memory
- Decode the instruction
-
Fetch data from memory (if required)
-
Execute the instruction
- Store
data to memory (if required)
- Move to
next instruction and repeat
Von Neumann receives
credit for the STORED PROGRAM CONCEPT - programs
are stored in
the same memory with the data, and the CPU can read the
program
commands via the same process that it reads the data. The
SINGLE
CPU is now considered a severe limitation. Modern
systems use multiple
CPU's to accomplish PARALLEL PROCESSING -
the limitation of a single CPU
is called Von Neumann's
Bottleneck.
PARALLEL-PROCESSING
Dependence on a single CPU, executing instructions one at a
time, makes
the system slower than a PARALLEL-PROCESSING
system, where many CPUs
execute many different commands at the
same time. Slowness caused by a
single CPU is called the "Von
Neumann Bottleneck." In actual fact,
modern computers all
contain many processors - the graphics card
contains a
microprocessor which is constantly busy refreshing the
screen,
at the same time that the CPU is doing calculations and
giving
commands.
INTERRUPT
When many components are busy at the same time, and they want
to talk to
one another, one component will send an INTERRUPT
SIGNAL to get the
attention of another component. When you
press a key on the keyboard, a
microprocessor in the keyboard
interrupts the CPU, and the CPU responds
to this signal
(HANDLES the interrupt). Systems that depend on
interrupts are
called INTERRUPT DRIVEN. If too many interrupts occur in
a
short time, the system can get bogged down. If a device
interrupts a
second time before the first interrupt has been
handled, the system
might crash. To prevent system crashes due
to conflicting interrupts,
many systems assign PRIORITIES to
interrupts - for example, the disk
drive might have a higher
priority than the printer. Another method is
to DISABLE
interrupts - this means that no interrupts are permitted if
the
CPU is already busy handling an interrupt. For example,
a
disk-drive will probably disable interrupts until it is IDLE
(finished
reading or writing). An INTERRUPT FLAG REGISTER
contains bits which
enable or disable specific levels of
interrupts - e.g. during disk
access, keyboard interrupts
might be disabled. An INTERRUPT VECTOR
contains the address
of the subroutine which handles the interrupt.
POLLING
an alternative to interrupt driven systems. Rather than
waiting for
a keyboard interrupt, the CPU might actually test
each of the keys
on the keyboard periodically to see whether
it has been pressed.
This is an old-fashioned idea and no
longer popular, as it wastes
CPU time to check for events even
when nothing has happened. Interrupt
driven systems allow the
CPU to continue working without paying
attention to the
keyboard, until something actually happens.
CACHE
486 systems contain CACHE-MEMORY on the MOTHER-BOARD. The
CACHE is a
small amount of very fast memory which the CPU uses
for temporary
storage. Accessing the CACHE is faster than
accessing main-memory. The
CACHE loads and saves to main
memory in large BLOCKS, not a single byte
at a time. Pentium
chips have LEVEL I (e.g. 16 KB) cache which is
contained
directly in the CPU chip. A LEVEL II cache is larger (e.g. 256
KB)
and connected directly to the CPU on one side, and the RAM
on the
other side.
MACHINE INSTRUCTION CYCLE
Fetch, decode, execute, store. A machine language instruction
is
written as numbers (not letters). The CPU FETCHES an
instruction
by loading bytes from the memory. The instruction
is DECODED by
looking at BIT FIELDS to decide what kind of
operation (e.g. ADD or
MOVE) is to be performed, where the
OPERANDS come from (e.g. registers
or memory), and where the
result should be stored. The instruction
is then EXECUTED
(performed), and then the results are STORED in the
specified
place.
PIPELINE
a method to speed things up is to process instructions in
an
assembly line fashion. Several instructions are in the
pipeline in
various stages - DECODE, FETCH, EXECUTE, STORE.
The CPU
completes a different operation in each of 4
instructions,
simultaneously.
RISC
Reduced Instruction Set Computer - increases speed by reducing
the
variety and complexity of machine language instructions.
That was the
original meaning, but the term has expanded to
encompass many concepts
which attempt to speed up the CPU -
pipelining, parallel-processing,
cache-memory, etc.
BINARY
Base 2. In base two, the place values are powers of 2, digits
are 0,1.
128
64 32 16 8 4 2 1 <-- Place
values
10011010 = 1 0 0 1 1 0 1 0
= 128 + 16 + 8 + 2 = 154 decimal
This produces UNSIGNED
(positive only) integers from 0 to 255.
TWOS COMPLEMENT
To deal with SIGNED (+ and -) numbers, modern computers use
this binary system.
The HIGH ORDER bit (128) is treated as
negative, so it counts as -128.
In this system, a byte holds
a number between -128 and +127.
01010101 = 64 + 16 + 4 +
1 = +85
11010101 = -128 + 64 + 16 + 4 + 1 = -43
10000000
= -128
01111111 = +127
11111111 = -128 + 64 + 32 +
16 + 8 + 4 + 2 + 1 = -1
Two other systems (outdated - no longer used) for SIGNED
integers were
called ONE'S COMPLEMENT and SIGN AND MAGNITUDE.
ONES COMPLEMENT
A binary system where the leading bit counts -127. A byte
counts from
-127 to +127 ( 10000000 to 0111111) There are two
versions of zero -
either 00000000 or 11111111. The 11111111
version is called
"negative zero". This system was
popular in the 1960s and earlier, but
the programming problems
caused by the negative zero made it unpopular.
This system is
still used in a few main-frames.
01010101 = 64 + 16 + 4 +
1 = +85
11010101 = -127 + 64 + 16 + 4 + 1 = -42
10000000
= -127
01111111 = +127
11111111 = -0
SIGN AND MAGNITUDE
A binary system where the leading bit is simply a minus sign,
with no
value. The other seven bits tell the size (magnitude)
of the number.
Like the ONE'S COMPLEMENT system, there is a
negative zero ( 10000000 ).
01010101 = 64 + 16 + 4 + 1 =
85
11010101 = - ( 64 + 16 + 4 + 1 ) = -85
10000000
= -0
01111111 = +127
11111111 = -127
HEXADECIMAL
Base 16. Place values are powers of 16. The digits
are:
0,1,2,3,4,5,6,7,8,9,A,B,C,D,E,F (so $F = 15
decimal).
4096 256 16 1 <-- Place values
4A2F hex = 4 A
2 F = 4*4096 + 10*256 + 2*16 + 15*1
= 18991 dec
Conversion from binary to hex is easy -
group bits in groups of 4.
10011010 bin = 1001 1010 = $ 9
A $ 3 7 = 0011 0111 = 00110111 bin
OCTAL
Base 8. Digits are 0,1,2,3,4,5,6,7 . Place values are powers
of 8.
437 octal = 4*8^2 + 3*8 + 7 = 287
To convert
from binary to octal, group bits in groups of 3.
11001010
bin = 11 001 010 = 3 1 2 octal
RADIX
another term for base, as in base-16 and base-2
So decimal is radix 10, binary is radix 2.
RADIX POINT
In decimal, the separator between the integer and fraction
portions
of a number is called the decimal point. The general
term for this
(in any base) is the radix point. Notice that in
base n, the place
values are powers of n. The positive powers
are to the left of the
radix point, and the negative powers
are to the right, like this:
Decimal : 345.27 = 3*100 +
4*10 + 5*1 + 2*(1/10) + 7*(1/100)
= 3*10^2 + 4*10^1 + 5*10^0 +
2*10^-1 + 7*10^-2
Place values = 10^2 10^1 10^0 . 10^-1
10^-2 10^-3
100
10 1 . 1/10
1/100 1/1000
Binary : 101.011 = 1
* 4 + 0 * 2 + 1 * 1 + 0*(1/2)+ 1*(1/4)+ 1*(1/8)
= 1*2^2 +
0*2^1 + 1*2^0 + 0*2^-1 + 1*2^-2 + 1*2^-3
Place values =
2^2 2^1 2^0 . 2^-1 2^-2
2^-3
4
2
1 . 1/2 1/4
1/8
WORD SIZE
the standard size of a number in a computer, measured in bits.
It is
normally the same as the size of a REGISTER in the CPU.
Computers are
classified as 8-BIT, 16-BIT, 32-BIT, according
to the size of a word.
8-BIT - a register contains a
single byte. UNSIGNED numbers count from
0 to 255 (2^8-1), and
SIGNED numbers from -128 to +127 (2^7-1)
The Commodore 64 home
computer was an 8-BIT machine.
16-BIT - a register is
16-BITS WIDE. In this system, UNSIGNED numbers
count from 0 to
65535 (2^16-1), and SIGNED numbers range from
-32768 to +32767
(2^15-1). IBM-PCs with 8086 (XT) or 80286 (AT)
CPU's were
16-bit machines.
32-BIT - a register is 32 bits wide.
UNSIGNED numbers from 0 to 2^32-1.
The 80386 and 80486
microprocessors have 32-bit registers.
24-BIT - a register
is 24 bits wide, giving numbers from 0 to 2^24-1,
which is
about 16 million. Super VGA graphics cards provide 24-BIT
COLOR
("true-color"), meaning 16 million different colors. A
single
PIXEL is represented by a 24-bit number telling its
color. Then a
640x480 graphics screen needs 640x480x3 =
921,600 bytes.
64-BIT - the typical word-size for a
super-computer (e.g. a Cray I)
OVERFLOW
the error which occurs when a value is too big to store in the
specified variable type. For example, the maximum value of a
16-bit
signed integer is +32767.
UNDERFLOW
the error which occurs when a decimal value is too small to
store in
a floating point number. This actually means that the
negative
exponent is too large to store in the exponent
storage space.
If a 1 byte, signed exponent is used, then the
smallest number possible
is 1 x 2^(-128), because -128 is the
largest negative number which can
be stored in one byte.
ADAPTER
(interface card) - an extra circuit board used to connect a
device to
the CPU. It provides an INTERFACE, translating
signals so the computer
and the device can communicate
successfully.
PORT
a connection between the computer and an external device. This
is
basically a memory-locations which is "mapped" to
a connector. To
transmit or receive data, the computer uses a
memory-address to identify
the specific port. The SERIAL PORT
is used to connect to a mouse or a
modem. The PARALLEL PORT is
used to connect to the printer or some
other external device.
This is not the same as an adapter, which
connects directly to
the main bus and does not have a corresponding
memory address.
SERIAL PORT
A port with only one data wire, so it sends 1 bit at a time.
Modems use
serial ports, since a telephone wire is a single
wire and can carry only
one bit at a time. Actually, modern
modems cheat and use a variety of
frequencies, so they manage
to send 2 or more bits at the same time.
But the computer is
only sending a single bit to the modem.
PARALLEL PORT
A port with 8 data wires, so it can transmit an entire byte at
once.
Parallel ports are typically used by printers, but a
printer can also be
connected to the serial port. The wires
running next to each other
cause electro-magnetic interference
(inductance), so the signal is only
reliable over short
distances (a couple meters.) If a printer uses a
serial cable,
the cable can be 10 meters long or more and still deliver
a
reliable signal.
MACHINE LANGUAGE
(assembly language) The language which is actually used by
the
computer's CPU. Instructions are extremely primitive, and
each
instruction is represented by a number(s). Programmers
usually use an
ASSEMBLER, which translates "mnemonic"
codes such as "MOV AX,$1234" into
the equivalent
numbers for the machine language instruction.
HIGH LEVEL LANGUAGE
For example FORTRAN (the oldest,1960), COBOL, PASCAL, BASIC.
The
instructions are more powerful and easier to use than in
machine
language. Most programmers utilize high level
languages because they can
develop programs more easily and
quickly than in machine language, but
the resulting programs
do not run as fast as machine language programs.
MULTI-TASKING
running more than one program at a time. Actually, the
programs don't
really run simultaneously. Instead, each
program runs for a very short
time (e.g. a millisecond) and
then the next program gets its turn.
This short time is
called a "time slice". This allows users to switch
quickly and easily between various applications. Windows does
this,
but DOS does not.
MULTI-USER
A PC is set up for only one single-user. It might be used by
various
users at various times, but never more than one user
at one time.
Main-frames are generally set up to be by many
users simultaneously -
it could be hundreds or thousands of
users. Each user needs a
"terminal" communicating
with the main-frame. This allows hardware,
software, and most
importantly DATA to be shared among many users.
APPLICATIONS
(programs) Most computer USERS do not write programs. Instead,
they buy
a program which will do the desired job and simply
learn how to use it
properly. Some common types of
applications programs are: Word
processor - for writing
letters Data-base manager - for manipulating
databases
Spreadsheet - for planning budgets and doing economic
projections
CAD - Computer Aided Design, used be engineers to draw
machines
TOP-DOWN DESIGN
(hierarchical decomposition) process of breaking a problem
into pieces,
then breaking these pieces into smaller pieces,
until the pieces are
small enough to begin writing a program
to solve the problem. The pieces
become procedures in the
program.
EDITOR
a program which is used to write SOURCE CODE (program text)
and to make
corrections in the text. This functions like a
word processor, but
would not normally wrap text or reformat
paragraphs
COMPILER
a program which translates the SOURCE CODE (text) of a program
into the
equivalent OBJECT CODE (the machine language
version.) As the compiler
translates the program, it notes any
errors which it finds, such as
SYNTAX errors and TYPE MISMATCH
errors. These are called COMPILE-TIME
errors, since they are
detected during compiling.
INTERPRETTER
similar to a compiler, translates program text into the
machine language
equivalent. However, an interpretter
translates ONE line of the program
and then executes it, then
goes on to the next statement. A compiler
translates the
entire program, which is then run as a whole unit. Older
versions
of BASIC (such as GWBASIC) were interpretters, whereas
TURBO
PASCAL is a compiler. Compiled programs run much faster
than
interpretted programs, since each line is only translated
once.
DEBUGGING
the process of finding and correcting "bugs"
(errors). Compilers have
the advantage of speeding detection
of syntax errors, whereas
interpretters allow interruption of
a running program and thus speed the
correction of run-time
(value) errors.
COMPILE-TIME ERROR
An error which is detected by the compiler, before the program
starts
running. For example, Syntax errors (missing semicolon,
misspelling),
Type-Mismatch (3.5 DIV 0.5), Unknown Identifier
(undeclared variable).
RUN-TIME ERROR
Errors which cannot be detected by the compiler and only occur
when the
program is actually running, such as I/O ERRORS when
a file is missing,
DIVISION BY ZERO, BAD SUBSCRIPT and other
VALUE errors, STACK OVERFLOW
(infinite recursion), or an
infinite loop!
LOGIC ERROR
An errors which does not stop a program from compiling or from
running,
but which causes it to produce incorrect results.
These are errors
which the programmer has made in thinking
about the problem.
CASE TOOLS
Computer Aided Software Engineering - these are tools for
developing
software systems without typing programming
commands (code).
A Visual IDE is a common example. Other
tools include Library Managers
documentation systems, and code
generators. In Visual Basic, there
are also "wizards"
for generating application "frameworks".
DBMS
Data Base Management System - a complex system for creating
data-files,
input forms, queries (searching and selecting),
and reports.
Sophisticated data-base applications can be
constructued without
programming (coding).
FILE
A collection of information, stored on a disk or tape drive.
It could
contain either DATA or a PROGRAM.
PROGRAM FILE
Contains a computer program, written in PASCAL or BASIC or
MACHINE
LANGUAGE or some other programming language. This is a
list of
instructions - things for the computer to do. This
could be a source
file, which contains text which must be
compiled, or in could contain
executable file - a machine
language program, either .EXE or .COM file
in MSDOS. A SYSTEM
file (.SYS) contains the operating system programs
which are
loaded when booting up. An OVERLAY file contains part of
a
program which will be loaded in only when needed - it cannot
run by
itself, only when loaded as part of another program.
DATA FILE
A file which contains data, such as names, addresses, phone
numbers.
This is information which can be read, but is not a
program - that is,
it does not tell the computer to DO
something.
RECORD
A group of data belonging together, all about one individual.
A file is
made up of some number of records. The number of
records in the file is
the "filesize".
FIELD
One single piece of information - part of a record. A record
is made up
of several fields (or perhaps only one).
FIXED LENGTH
A field may have a fixed length - a maximum size. Regardless
of what is
actually stored in the field, it will still occupy
the same amount of
space. Random-access files generally use
fixed-length fields.
VARIABLE LENGTH
A field is saved ending with a control character. This way the
field can
be arbitrarily long. This saves memory in the long
run, since no empty
space is saved. Text-files use
variable-length fields, each line of
text ending with #13
(carriage return) + #10 (line feed.)
SEQUENTIAL ACCESS
(serial access) Reading the data in order, from beginning to
end.
Thus, to read the 10th record, it is necessary to read
the first record,
second record, ..., ninth record, and then
finally the tenth record.
This is VERY SLOW, but it is
possible to use variable record lengths,
and thus saves space.
TAPE-DRIVES use sequential access.
SERIAL FILE
A data file which must be accessed sequentially, in which the
records
are not in any specific order. A text file is an
example.
SEQUENTIAL FILE
A data file which must be accessed in order, even though the
records
are SORTED in a specific order. It might be necessary
to read them
in order because the records are variable sizes,
so there is no
way to "jump" to a specific place.
RANDOM ACCESS
(direct access) A file in which it is possible to read the
10th record
directly, without first reading the other 9. This
is faster than
sequential access, but requires a fixed record
length, since the
location of the record on the disk must be
calculated. This wastes space
but saves time. DISK-DRIVES are
random access devices.
INDEX
a separate file which tells where certain records in a data
file are.
The index will be for a particular KEY FIELD, and
will contain POINTERS
which are record numbers in the data
file. For example, the NAMES of
customers might be recorded in
an index, so that the customers can be
printed alphabetically.
It is possible to create an index for each
field, without
needing to change the physical order of the data file.
The
data file can be SORTED on different KEYS without being
rewritten.
HASHING
a KEY FIELD contains a value from which the POSITION of the
record in
the file is calculated. The birthday could be used
as a key field. But
since some birthdays will not appear in
the file, there will be empty
records (dead space). And since
some birthdays appear twice, there can
be "collisions".
Hashing is very fast, but exacts a considerable
penalty in
wasted storage space.
GLOBAL VARIABLE
a variable declared at the beginning, whose value is used
throughout a
program and all of its procedures. Global
variables are dangerous, as
they can result in SIDE-EFFECTS
where two different procedures use the
same variable for two
different purposes.
LOCAL VARIABLE
when a variable is declared inside a procedure, its value is
only
available LOCALLY - inside the procedure. This allows the
same name to
be used in two different places and have two
different values.
PARAMETERS
the data (numbers or strings) which are given to a procedure
when it runs
Passed by VALUE (input only) - the value of the
parameter is copied
and a second copy stored separately inside
the procedure
Passed by REFERENCE (VAR input/output) - the
address of the parameter
is given, and the procedure does not
make its own copy of
the value
ALGORITHM
a process or strategy or method for solving a problem. A good
one is
efficient - runs as fast as possible or uses as little
memory or storage
as possible, or both.
BIG-O NOTATION
the proper method for measuring the speed of an algorithm. The
actual
time required for an algorithm is not a good measure of
speed, because
this will be different on faster machines than
slower machines, and will
also change according to the
specific data. Speed = O(n^2) means that
if the average
execution time is graphed for a various amounts of data,
then
the shape of the curve will be like the graph of y=n^2 . In
simple
terms, if the length (n) of the list of data is doubled
(*2), then the time
will increase by *2^2 .
SORTING
the process of putting a list of data items in order. When a
file is
sorted, the records are put in order according to the
KEY field - this
will contain an identification number or
name.
BUBBLE SORT
go through the list, switching neighbors which are out of
order. This
is repeated until no more switches are necessary.
Speed = O(n^2)
SELECTION SORT
Find the smallest item and SWAP it with the first item. Find
the second
smallest item and SWAP into position two, etc.
Speed = O(n^2)
QUICK SORT
separate the list into two halves, a smaller half and a larger
half.
Then do the same to the first half, and then to the
second. Repeat this
on ever smaller pieces of the list until
the pieces contain only one or
two elements. Speed = O( N Log
N )
BUCKET PRESORT
(categories) this is an approximate sort, putting the items
into
categories. For example, a list of words can be presorted
by putting all
the A's first, then the B's, then the C's, etc.
This requires only one
pass, through the list and thus goes
quite quickly. After presorting, a
bubble sort will be MUCH
faster. Speed = O(N)
BINARY SEARCH
finding an item by deciding whether it is in the first or
second half of
the list, then repeating this with that half,
until the section to be
searched is only one or two items.
This is VERY fast, but can only be
done if the list is sorted
first. Speed O( Log N )+
SEQUENTIAL SEARCH
look through the records in order until the item is found.
This is a lot
slower than a binary search, but works on
unsorted lists.
MERGE
combine two files into one file - usually combining two SORTED
files
into a sorted file.
ARRAY
(matrix) a list of data, where the position of an item is
identified by
number (the SUBSCRIPT or INDEX). Arrays are
STATIC, meaning the total
SIZE never changes during program
execution.
DYNAMIC STRUCTURES
can grow and shrink as the program is running - including
trees, linked
lists, stacks and queues
LINKED-LIST
linear list of data where POINTERS point from one NODE to the
next.
Usually stored in the HEAP or some other flexible memory
area. The
beginning is called the HEAD and the end is called
the TAIL.
TREE
a linked structure where each PARENT NODE points to several
CHILDREN.
This "branching" behaviour differentiates
it from a linked-list.
STACK
linear data structure, LIFO = Last In First Out, use PUSH to
put a new
piece of data into the structure, use POP to
retrieve data
QUEUE
linear data structure, FIFO = First In First Out, use ENQUEUE
to put
data into the structure, use DEQUEUE to remove data
MAINFRAME
a large, expensive, fast computer designed to be used by many
different
users. They usually have many peripheral devices
attached and a
particularly large capacity in the storage
devices. A smaller, cheaper
version is called a MINICOMPUTER,
which also has many users. A very
FAST mainframe is called a
SUPERCOMPUTER.
MICROCOMPUTER
(personal computer, home-computer, work-station, stand-alone)
A small
computer designed for just one user, usually slower,
smaller, cheaper,
and with less storage than a mainframe or a
minicomputer. Modern PCs are
as powerful as minicomputers were
20 years ago.
INTERACTIVE
a computer system where the USER(s) is directly involved when
the
program is running - typical for microcomputers
BATCH PROCESSING
(non-interactive) a large set of data (or programs) are
ALL
processed without a user being involved - typical for
mainframes.
This is the opposite of on-line processing.
ON-LINE
entering data and commands directly into a computer system.
The
system reacts immediately to the user's input.
This is
the opposite of batch-processing.
REAL-TIME
a computer system which must react to input in a specific
limited
amount of time, keeping up with the environment. An
air-traffic-
control system is a prime example. This is not
the same as on-line
systems, which could get busy and react
slowly. If an air-traffic-
control system gets busy, it cannot
postpone decisions until later.
MASTER FILE
the main file in a database system - the permanent storage of
the
data. In a bank, this would contain the customer
addresses and
balanaces. Contrast this with a transaction
file, which only
contains single, daily activity, such as a
withdrawal or deposit.
TRANSACTION FILE
contains single activity records, such as deposits and
withdrawals
from a bank acount. These records are the POSTED
to the MASTER FILE.
In a batch-processing system, this file
builds up throughout the day,
and then all the records are
posted to the MASTER FILE at one time
at the end of the day.
OPERATING SYSTEM
the collection of programs and subroutines which control the
hardware
directly - turning the disk-drive motor on and off,
reading the keys
which are pressed on the keyboard, putting
graphic displays on the
screen, etc. This has two parts - a
Built In Operating System (BIOS)
located in ROM, and the rest
of the operating system which is loaded
from the disk and
resides in RAM. Popular systems are MSDOS for PC's,
SYSTEM 7
for MacIntosh, UNIX for mainframes. An OS used only by
one
manufacturer is called PROPRIETARY - i.e Apple's System 7.
LINKER
a utility which combines separate program modules into an
executable
program.
LOADER
the part of the operating system which loads an executable
program
into the memory and then starts it running. The user
double-clicks
on the icon in Windows 95 to start a program, so
they don't think
of this as a separate utility. However, in
some operating systems
a specific command must be typed to
load and execute a program.
LIBRARY
a collection of re-usable sub-programs (subroutines) which can
be
used in various program. For example, a good sorting
routine
might be included, so that programmers don't need to
waste time
writing their own. Presumably these routines have
been thoroughly
tested and are very reliable and efficient.
They must also be
thoroughly documented.
DOS
Disk Operating System. This is a program which controls all
disk
access. It automatically allocates space on the disk,
keeps the
directory updated, and does all of the reading and
writing of files. It
keeps track of which sectors on the disk
are currently in use, and which
file is using each. This way,
the application programs do not need to
bother worrying about
the physical structure of the disk.
TIME-SHARING
a system in which many users can run programs simultaneously.
The
computer memory is divided into sections, and the CPU
jumps from program
to program, running a little bit of each
one. Each user has a
DUMB-TERMINAL (not a PC) to communicate
with the main computer.
LAN
Local Area Network. A bunch of PC's (perhaps also mainframes)
near each
other (same building) connected by wires, which
share data and programs.
Each user has a computer on his/her
desk. A central computer, the
SERVER, stores programs and
data. When the user wants to run a program,
the program is
"down-loaded" from the server to the PC and runs in
the
PC's memory. It can access data files on the server. The
PC can also
use LOCAL programs and data, stored on the "local"
disk drive. LANs use
DEDICATED wires which are used ONLY by
the network.
WAN
Wide Area Network (Long Haul Network). The computers in a WAN
are far
apart from each other, and these are generally
main-frames. A large
bank may have mainframes in each major
city, which need to be connected
to each other to exchange
financial data. Although programs COULD be
downloaded, WANs
generally only transmit data. There is usually no
"central"
computer. Usually communication is over telephone lines.
TOPOLOGY
the basic structure of a network. The three most common types
are:
ring, bus, and star.
HUB
a central connector where many cables can be plugged in,
connecting
many computers together. Star networks use these,
bus networks do not.
These are very stupid devices, and simply
repeat incoming signals to
all the connections.
SWITCH
a smarter version of a hub, which "knows" where a
packet should go,
and thus sends the packet to the correct
connection, without bothering
the other connections. This
routing function is limited to a single
network section.
ROUTER
a very smart version of a switch, which can send packets to
the
the correct destination in more than one network. These
are expensive
devices, usually purchased to connect two
networks together.
NODE
any computer or other device in a network - a workstation, a
server,
or a networked printer.
CLIENT-SERVER
a network in which shared data is stored in a dedicated
server.
Any communication between workstations would always
pass through a
server. This requires a network OS such as
Novell or NT or Linux.
This generally provides more efficient
service and better security
(through accounts and passwords)
than a peer-to-peer network.
PEER-TO-PEER
a network in which communication passes directly from one
workstation
to another, without involving a dedicated server.
A workstation
can "share" it's disk drive, allowing
other workstations to access
files. This is cheap and simple
to set up and use - Windows 95
supports this simple
networking concept. However, there are no
"accounts",
so there is only very simple security - files can be
read-only
or full-access - no way of permitting access to
specific
users.
BUS NETWORK
a network which uses one single cable to connect many
computers.
The common example uses BNC connectors and coaxial
cable, attaching
one connector to each network card, and using
one more section of
cable to connect to the next computer.
This has slow performance,
as only one single computer can
transmit at one time, as there is
only one cable. It is also
less reliable than a star network,
as one single defect in the
cable stops the entire network.
STAR NETWORK
a network which uses a single cable for each computer,
attaching it
to a central hub. The common example uses UTP
(unshielded twisted
pair) cables. This is faster and more
reliable than a bus network,
but more expensive (uses a lot
more cable and requires the hub to
be purchased) and less
flexible (cables must be a specific length
and must run to the
hub, so adding a new computer is more trouble.
TOKEN RING
Similar to a star network, but communication is managed by a
central
controller, which decides which computer is currently
allowed to
transmit. This can be quite efficient, but is
fairly expensive and
requires more management than star or bus
networks.
HYPER-TEXT
the ability to jump from one part of a document to another
part of the
same document, or indeed to a totally different
document. This linking
of text increases to value of the text,
as it makes connections between
ideas and information.
HYPER-TEXT-MARKUP-LANGUAGE
HTML - the rules for the internal structure of World-Wide-Web
pages.
This has a very specific set of syntax rules, thus is
similar to
a programming language. Variables, arithmetic, and
loops are not
supported, so it is not a "true"
programming language. Nevertheless,
HTML gives "commands"
to the browser, much in the same way as a
programming
language gives commands to the computer.
SEARCH ENGINE
A web-site which accepts requests from a user, consults a
database
of web-pages categorized by topic, and produces a
list of web-pages
matching the user's request.
ELECTRONIC MAIL
a network of computers in various locations, in contact with
one another
via telephone, which send messages from one
computer to the next and
further until they arrive at their
destination. Can move a letter around
the world in less than a
minute.
DATA LOSS
data (or software) is erased, corrupted, or
destroyed
ACCIDENTAL = due to hardware failure, software
error, or user mistakes
MALICIOUS = intentionally caused by a
HACKER, or a ROGUE PROGRAM such as
a VIRUS or a TROJAN HORSE.
PIRACY
the unauthorized (illegal) copying, use, or sale of
software.
This is a big problem in the PC software industry,
where software is
widely distributed on floppy diskettes, and
therefor can very easily
be copied and used without payment.
HACKING
"breaking in" and using a computer system without
permission.
This is a bigger problem in mainframe systems and
computer networks
than in the PC world. Hacking originally
meant something quite
different - it meant spending time
looking for exceptionally clever
solutions to computer
problems. A "good hack" still refers to a very
clever
program, or designing a clever hardware device.
PRIVACY
confidential data should only be ACCESSED by AUTHORIZED
users.
This is a big problem when personal data are stored in
large databases.
BACKUP
an extra copy of software or data files. This is the best
protection
against data loss, since the data or software can
be completely
recovered, regardless of what caused the loss.
Backup copies should
always be stored away from the computer -
in a different building if
possible, to avoid catastrophes
such as fire. Backups are effective
against data loss, but
actually work against privacy, since the extra
copy is just
another security risk.
PHYSICAL SECURITY
computers and terminals are locked up, either in locked rooms
or through
locks on the computers. Also, the environment is
kept free of fire
risks, electromagnetic fields, dust, and
excessive heat. Physical
security can be effective against
hacking, but difficult to implement in
a large system or a
network.
SOFTWARE SECURITY
an operating system may prevent access by unauthorized users
through the
use of PASSWORDS or other identification
procedures, such as ID cards,
voice patterns, fingerprints,
handwriting recognition. This is the
preferred method to
protect against hacking, as it can be implemented
regardless
of the physical size or location of the system.
PRIVILEGE
Large computer systems assign a privilege level to each user,
so that
not all users are permitted access to everything.
SUPERVISOR or SYSOP
(system operator) is usually the highest
level, and has access to
virtually everything. These security
levels are usually enforced by the
operating system.
DONGLE
an extra device (key or circuit card) which must be inserted
in the
computer before use. Some software packages include
dongles as a
protection against piracy.
ENCRYPTION
Data files are stored in a "secret code", and can
only be decoded
by someone who knows the KEY (the secret). DES
(Data Encryption
Standard) is a widely used system in the
United States. The ENIGMA
machine was an encryption system
used by the German army during World
War II to encode radio
and written messages. Alan Turing, of Turing
Test and Turing
Machine fame, worked on the British COLOSSUS project, a
computer
to DECRYPT (decode) Enigma. The success of this project
was
instrumental in winning the war.
TRACK
a circular piece of disk storage - a floppy has 40 or 80 tracks.
SECTOR
part of a track on a disk-drive. A track might have 16 sectors
of 512
bytes each.
CLUSTER
Disk sectors are not allocated one at a time, but in clusters.
On a
hard-disk, the cluster size might be 2, 4, or 8
kilobytes. In MSDOS,
clusters are numbered from 0 to 65536. So
a 512 MB hard disk has a
cluster size of 512 MB/64 Kb = 8 Kb.
This means that if you write a
small batch file, containing
1000 characters, it will still occupy an
entire cluster (8 KB)
so there is 7 KB of wasted space.
DIRECTORY
a list of file names. In MSDOS and Windows, the files are
grouped into
subdirectories, to try to keep things organized
in a rational fashion.
FAT
File Allocation Table - keeps track of which clusters have
been
allocated, to which file, and which clusters are still
free.
HARD-DISK
the standard system is called a WINCHESTER DRIVE. This
device
contains several PLATTERS (disks), stacked on top of
each other, with a
SPINDLE (axle) in the middle. There is a
READ/WRITE HEAD for each SIDE
of each PLATTER. These heads are
on metal arms which move the heads in
and out to ACCESS
different CYLINDERS (tracks). The head must SEEK the
track and
SETTLE (stop moving and vibrating) before reading or writing.
All
arms/heads move together as a single unit (the COMB). A
STEPPER
MOTOR moves the heads from one track to the next. When
the disk drive
is turned off, the heads are moved to a LANDING
ZONE, a track which is
not actually used for data storage.
This is because the heads actually
touch the disk when it
stops rotating. When the computer starts up, the
drive must
SPIN-UP to normal operating speed (several thousand RPMs).
The
movement of air caused by the spinning disk causes the heads
to
float very close to the surface of the disk without
actually touching.
BOOT-SECTOR
the first sector on the disk, contains a BOOTSTRAP-LOADER
program which
simply loads the Disk-Operating-System files
from the disk drive and
executes them.
FORMAT
a disk must be formatted before it is actually used. This
places
TIMING-MARKS at the beginning of each sector, together
with a sector ID
mark. When the drive is SEEKING a sector, it
watches for the timing
marks, then reads the sector ID which
follows, and reads the data which
follows.
INTERLEAVE
Sectors 1,2,3,4... might be stored sequentially next to each
other in a
track. But if the disk is spinning very fast, the
CONTROLLER might not
be able to process the data from sector 1
quickly enough to be ready to
read sector 2 when it comes
along. As a result, the controller will
need to wait an entire
revolution before sector 2 comes by again. To
compensate, the
sectors can be interleaved like this: 1,5,2,6,3,7,4,8 .
Then
the controller has enough time between sectors, since there is
an
entire sector between sectors 1 and 2. This is called a 1:2
interleave.
If the sectors are stored in order, it is called a
1:1 interleave. When
an advertisement claims 1:1 interleaving,
it is a promise that the
controller can read fast enough to
keep up with the spinning disk. Disk
drive performance can be
signicantly enhanced by choosing the proper
interleave when
formatting the disk.
MEAN ACCESS TIME
(mean seek time) the average amount of time for the head to
move to the
proper track and reach the desired sector. Typical
for a hard-disk is
20 ms (milliseconds). Smaller hard-disks
(notebook computers) usually
have faster access times, since
the heads move a smaller physical
distance. ACTUAL seek time
is variable, depending on current head
position.
LATENCY
rotational delay. When a disk drive seeks from one sector to
another,
it needs to move the head to a different track, and
then wait for the
spinning disk to bring the correct sector
under the head.
SEEK
a disk drive must move the read/write head and wait for the
disk to
rotate in order to find a new sector. A typical seek
time is
0.1 milliseconds.
TRANSFER RATE
the speed of transmitting data from a disk drive to memory
(or vice versa).
CONTROLLER
a cirucit board which directly controls a hardware device. An
IDE
interface is a card (or part of a mother board) which
controls the
disk drive directly, turning on the motor, moving
the heads, etc.
Programs give very high level commands to the
controller (e.g.
GET #1,,info), which are then translated into
specific commands to
the physical device.
DEFRAGMENTATION
if a file is stored in clusters which are scattered all over
the disk,
then access will be very slow. This utility program
relocates files
into CONTIGUOUS (adjacent) sectors. This
problem mostly occurs when
a disk is fairly full and a lot of
erasing and recopying is being done.
MONOCHROME
Black and white monitor, no colors. Colors are represented in
GRAY
SCALE (varying shades of gray). Common is 16 or 32
gray-scales.
PIXEL
the smallest dot which can be drawn on the screen - an
abbreviation for
Picture Element.
BIT-MAPPED GRAPHICS
(raster graphics) pictures are stored pixel by pixel. The
color of each
pixel is stored in the memory, normally in V-RAM
(video RAM) located on
the GRAPHICS CARD (adapter). The total
number of colors (PALLETTE)
depends on how many bits are used
to store each pixel. If 4 bits are
used for each pixel, then
2^4 = 16 colors can be represented. TRUE-COLOR
graphics cards
offer 24-BIT COLOR, which provides 2^24 = 16 MILLION
colors.
Pixels are arranged in a RASTER (matrix) of SCAN
LINES
(horizontal) divided into individual pixels.
RESOLUTION
the number of pixels on the screen. HIGH-RES means lots of
pixels,
LOW-RES means not so many pixels. Typical resolutions
are:
1024x768 (Super VGA) 640x480 (VGA) 640x350 (EGA)
VECTOR GRAPHICS
Lines and curves are stored, instead of individual pixels. For
example,
a vector (line) is represented by storing the
coordinates of its
endpoints, which means storing 4 numbers.
This is much more efficient
than storing the color of every
pixel on that line. A "true" vector
graphics monitor
does not draw individual pixels at all. Instead, it
moves the
electron gun around the screen actually drawing the vectors
and
curves required. This system is much more complex (expensive)
to
build and program, and is not used in PC's. This produces
perfectly
straight lines and smooth curves, with no JAGGIES
(stair-step effect).
Another advantage is that rotating a
vector requires only 4 numbers to
be recalculated, whereas
rotating a pixel-representation requires EVERY
PIXEL to be
recalculated. Vector graphics screens are used in expensive
CAD
systems, which require extremely high-quality displays, and
in
SIMULATORS which require REAL-TIME rotations of pictures.
PLOTTERS use
vector-graphic logic to draw pictures. Printers
are bit-mapped.
REFRESH
the picture on the monitor is redrawn about 60 times every
second. The
electron gun draws one SCAN LINE (horizontal),
then moves down to the
next, then down again, until it reaches
the bottom of the screen. It
moves back up to the top -
VERTICAL RETRACE - and scans the entire
screen again. This is
a fairly continual process. Fortunately, the
graphics card
controls the monitor without the help of the CPU -
otherwise,
the CPU would be constantly busy redrawing the screen.
INTERLACED
If too many scan lines are required, the refresh takes too
long. The
image FLICKERS because the pixels at the top are
already fading out
before the refresh finishes at the bottom.
Below 50 Hz (refreshes per
second) is too slow and our eyes
notice the flickering. To fool our
eyes, the monitor can use
interlacing - it draws a scan line, then skips
one, then draws
one, etc., leaving out every second line. It then goes
back to
the top and draws the rest of the lines. One complete refresh
is
done in two passes. This allows refresh rates around 30 Hz
without
the user noticing flicker. Faster, more expensive
monitors display
HI-RES modes without interlacing
(NON-INTERLACED).
ANTI-ALIASING
Jaggies are especially bad at the edge of an object - i.e.
where a red
circle meets a blue background. By making the
pixels near the edge
change colors more gradually - red,
purple, violet, blue - the jaggies
become less noticeable,
although the edge becomes fuzzy. This must be
performed by the
software, not the monitor or graphics card.
BAUD
The basic speed of the modem's signal, similar to the MegaHerz
of your
micro-processor. This is the speed at which the signal
can change.
Voice-phone lines can accomodate signal changes up
to 2400 times per
sec. This does not mean the same as
bits-per-second, especially if
noise in the line causes lots
of retransmissions, or if data-compression
is used.
BPS
Bits Per Second - The DATA-TRANSFER RATE may very well be
faster than
the BAUD rate. By using clever methods such as
phase-changes, a modem
can send 16 different types of signal,
thus encoding 4 bits into each
signal change. Then at 2400
BAUD, it transmits 2400*4 = 9600 BPS.
COMPRESSION schemes can
further increase the data-rate.
PROTOCOL
Two modems need to agree on the details of data transmission,
and
this involves a lot more than just the BAUD rate. The
entire set of
rules and details is called the PROTOCOL. A
common standard is V.32.
DUPLEX
The ability to transmit data in two directions. Full-duplex
means that
data can be transmitted in both directions at one
time - telephones are
full-duplex. Half-duplex means that data
can be transmitted in only one
direction at a time -
walkit-talkies and police-radios are half-duplex
devices. When
using a modem, if you select Full-Duplex, then when you
type a
character it will not appear on your monitor until it has
been
transmitted and echoed back by the other computer. In
half-duplex mode,
the character is immediately printed and
then transmitted. A common
problem with modems is that you are
in half duplex-mode, but the other
computer is echoing, so you
see all the characters appearing double on
your screen.
A
SIMPLEX system does not allow transmission in both
directions.
Television signals are simplex signals - the TV
set does not transmit
information back to the television
station.
ASYNCHRONOUS
Not Synchronized - when typing, you transmit only a few bytes
per
second. When no data is being transmitted, the line is in
IDLE mode,
which means the line is held HIGH. A START-BIT
(line goes low) signals
that a DATA-BYTE is about to be sent.
DATA-BITS are then sent (high=1,
low=0), followed by a
PARITY-BIT, then 1 or 2 STOP-BITS. During this
time the
communication is synchronous - transmit and receive at the
same
speed (i.e. 9600 bps). After the stop-bit(s), the line
goes back to high
(IDLE).
<-------- Data Bits
----------> parity
bit
IDLE 1 0 1 1 1 1 0 0 1 1
IDLE
High -------+ +---+ +---------------+
+-----------------
| | | | | | Stop
Low +---+ +---+
+-------+ bit(s)
Start
bit
HANDSHAKING
(protocol) One needs an orderly process to ensure that data
is
transmitted only when the receiver is ready for it. The
computer must
be sure that the transmitting modem, telephone
line, and receiving modem
are all ready before attempting a
transmission. Several control signals
are exchanged before
transmission begins, including:
Data Terminal Ready (DTR)
Request to Send (RTS)
Data Set Ready (DSR) Clear to Send
(CTS)
Data Carrier Detected (DCD) Transmit Data (TD)
Ring
Indicator (RI) Receive Data (RD)
A typical sequence might
be:
DTR - Computer tells modem it is turned on
DSR - Modem
tells computer it is attached to a telephone line
RI - The
modem senses the phone is ringing
DCD - The modem says it is
attached to another (remote) computer
RTS - Computer says it
wants to send some data
CTS - Modem tells computer okay, it
can start sending now
TD - Computer transmits data, which the
modem sends to other computer
Different manufacturers use
different systems for these signals. For
example, after a DTR,
the modem might be required to wait 1 millisecond
and then
send a DSR.
ISDN
Integrated Services Digital Network - an international
communications
standard for sending voice, video, and data
over special telephone
lines. This requires special wires and
transmits 64,000 bps. A future
version, B-ISDN, will use
optical fibers and transmit 1.5 million bps.
PARITY-BIT
A an error-detection scheme, using a single bit for each byte.
For each
byte, the computer counts up the 1 bits in the byte,
and then sends
an extra bit telling whether the total should
be odd or even. If a bit
gets CORRUPTED during transmission,
the parity bit won't match at the
other end, and the other
computer can ask for a re-transmission. For
example, instead
of sending the 8 bits 11001010, you would send the
9 bits
11001010-0 . The extra bit is the parity bit, saying that
there
were an even number of 1's in the data byte.
EVEN-PARITY
In this system, the total number of 1's in 9 bits
(including
the parity bit) is always even. Thus, 11001010:0 is
transmitted.
ODD-PARITY
Here the parity bit is exactly the opposite of
even-parity
systems. When there are an odd number of 1's, a 0
parity bit is sent.
Thus the total number of 1's in 9 bits is
ALWAYS ODD. For example,
11001010:1 is a valid transmission.
Odd-parity is more reliable than
even parity - if the line is
suddenly disconnected, the other computer
might think it is
receiving 000000000000.... Under even-parity, this
appears to
be valid, but under odd-parity it is obviously not valid. A
total
disconnection is a common problem, so odd-parity is a far
better
system. In any case, both computers must AGREE what
sort of parity-check
is being carried out. The 3 choices are:
Even, Odd, or None.
VALIDATION
checking whether entered data is REAONABLE - could possibly be
correct.
Common methods are RANGE CHECKING (e.g. ages must be
between 1 and 120)
and TYPE CHECKING (e.g. if a name was
required, the user should not
type any numbers. This does not
guarantee the data is correct, but
failure does mean the data
is wrong.
VERIFICATION
checking whether entered data is actually CORRECT. This is
usually
accomplished by LOOKING UP the value in a data file,
cross-referenced
against some other data. For example, if a
bank customer types their
NAME and PIN code, the two must
match the data stored in the bank's
database.
MULTIPLEXING
using a single data-line to carry on several conversations
at
the same time. FREQUENCY multiplexing mixes many different
frequencies.
TIME multiplexing interleaves the converstations,
giving a short amount
of carrier time to each signal in turn
(PACKET-SWITCHING).
START-BIT
before a byte is transmitted, a start-bit alerts the receiver
that data
is coming. This bit is only a signal - not data.
STOP-BIT
20 years ago, terminals were TELETYPES, which were very slow
mechanical
devices. There needed to be a delay between bytes,
and this was
accomplished by sending stop-bits. Today, you can
still choose 1 or 2
stop bits, although their original purpose
is no longer relevant. But
many mainframes have been around
for more than a decade and thus use
stop-bits, so they
continue in use for purposes of compatibility.
ANALOG DATA
a signal which can vary continuously from small values to
large values,
with no specific "steps" in between.
Typcial for temperatures sensors.
This must be converted to
DIGITAL form before it can be stored or
processed by a
computer. Another example is sound waves.
DIGITAL DATA
a signal which changes in very specific STEPS (intervals).
Thus, rather
than 1.2345642, the value might be rounded off to
1.23. Money is
digital, having an exact number of pennies.
Sound waves are NOT like
this - they have continuous
variations, rather than stepped variations.
When a computer
wants to generate sound, it must convert its
digital
representation to an ANALOG signal which then produces
sound.
ANALOG-DIGITAL CONVERTER
ADC - converts continuous signals to discrete signals, thus
turning
a smooth curve into "stair steps". A sound
card uses this to
change sound-waves into digital signals for
storage and transmission
in computer sytems.
DIGITAL-ANALOG CONVERTER
DAC - converts discrete signals (bits) into continuous
signals.
A sound card changes the bits from a computer file
into continuous
sound waves and transmits these to a speaker.